Research
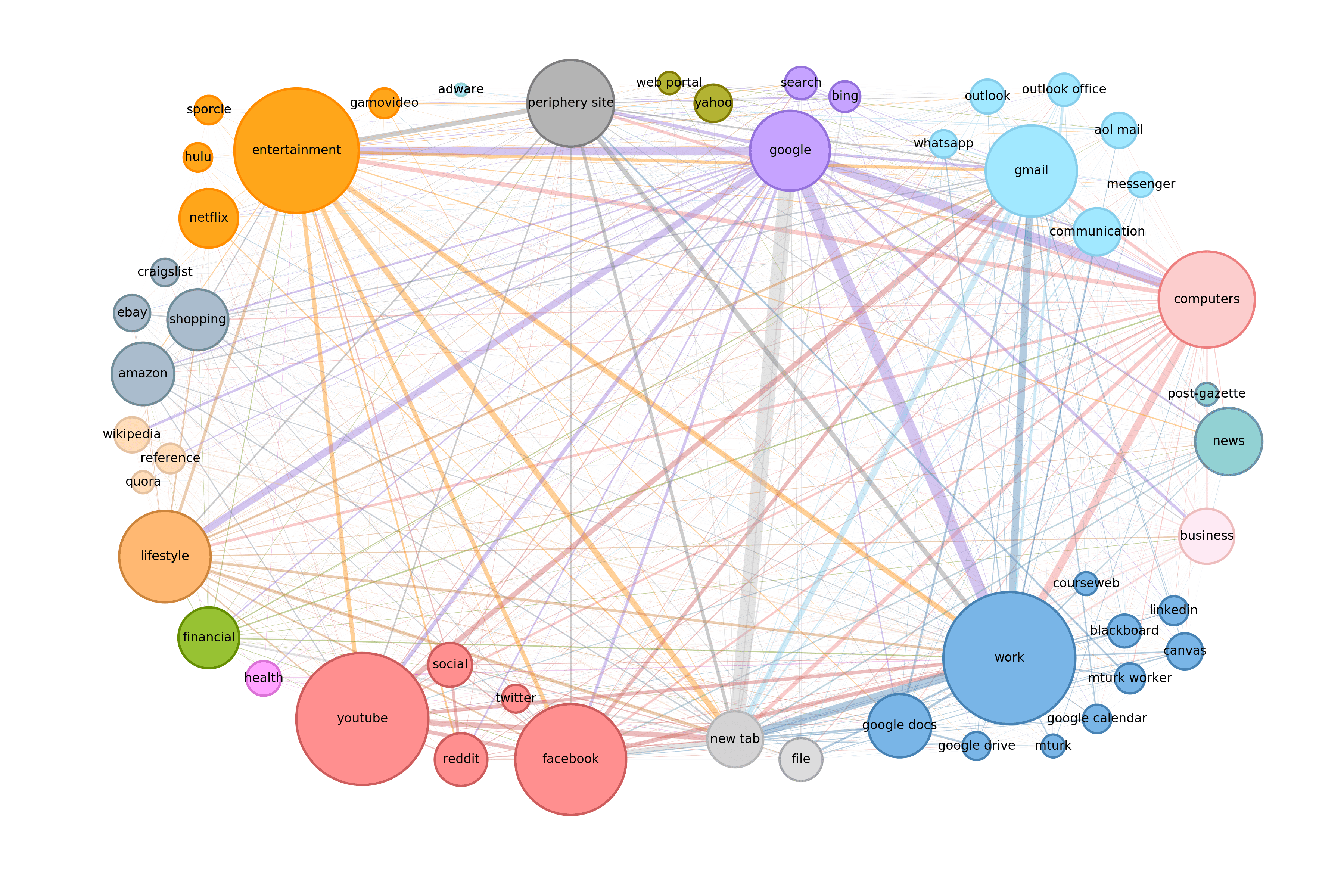
Data on how people browse the web is abundantly collected, but rarely distributed due to its proprietary nature. As a result, our understanding of user web browsing primarily derives from a set of small-scale studies conducted over a decade ago. Using resources like the Security Behavior Observatory, this work provides a more detailed and recent snapshot of user browsing patterns allowing us to better understand how people navigate and spend their time online. We find that user browsing is highly centralized, with over 50% of browsing time dedicated to a mere 32 websites. However, users also spend a disproportionate amount of time on websites ranked outside of the top 10 million, areas known to have a higher risk of containing risky and malicious content.
Kyle Crichton, Nicolas Christin, and Lorrie Faith Cranor. How Do Home Computer Users Browse the Web? TWEB 2022. View Here
Akira Yamada, Kyle Crichton, Yukiko Sawaya, Jin-Dong Dong, Sarah Pearman, Ayumu Kubota, and Nicolas Christin. On recruiting and retaining users for security sensitive longitudinal measurement panels. SOUPS 2022. View Here
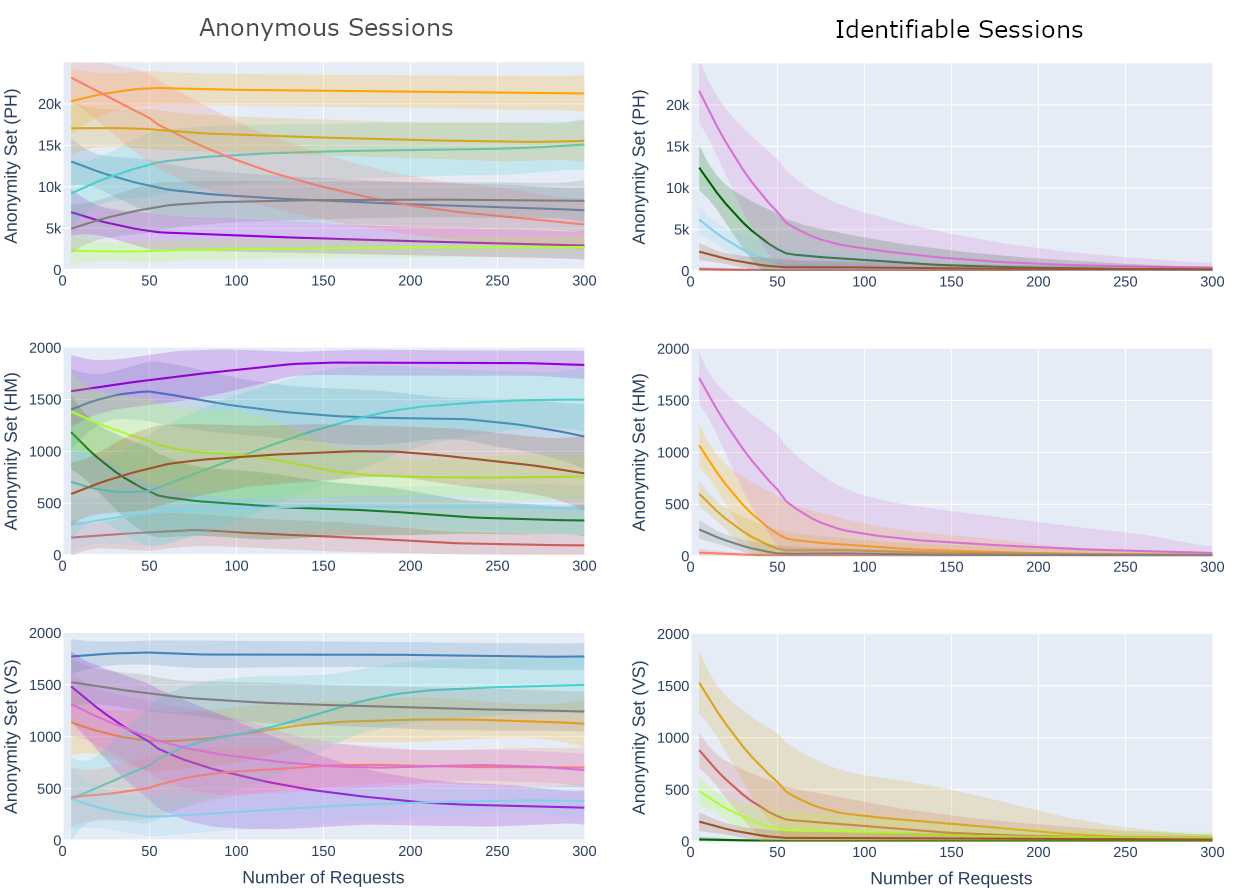
In this study, we provide the first analysis of behavioral fingerprinting at scale, with upwards of 150,000 users across two years. We find that while performance decreases with scale, the marginal performance loss becomes minimal for samples larger than 25,000 users. Optimal performance is achieved when a tracker has observed 15-25 prior browsing sessions, however the classifier can still reduce the size of the average anonymity set by 84-95% relying on a single previous browsing session. Using these techniques, a user loses an average of 78-85% of their anonymity within the first 60 seconds of coming online and 90% anonymity within the first 10 minutes of browsing. Combined with browser fingerprinting, our model can achieve an F1 score of 0.869 across 100,000 users.
Kyle Crichton, Nicolas Christin, and Lorrie Faith Cranor. Rethinking Fingerprinting: An Assessment of Behavior-based Methods at Scale and Implications for Browser Fingerprinting. 2023. In Submission.
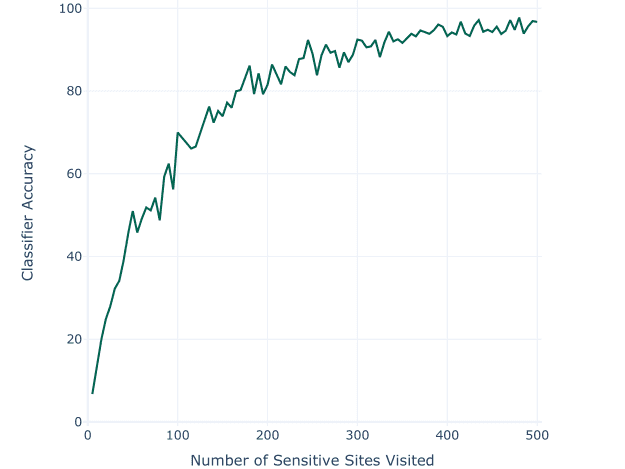
Despite the absence of explicit indicators of sensitive characteristics in online advertising profiles, numerous cases of discriminatory advertisements targeted on the basis of race, gender, sexual orientation, and history of substance abuse exist. In this study, we empirically demonstrate the existence of a previously unidentified vulnerability (inference of sensitive browsing from innocuous profile labels) in a widely-employed system (behavioral profiling conducted by a large data aggregator) that could be exploited by any customer of the platform at low cost to target sensitive web users. Using 30,000 web browsing simulations and their associated profile information, we find that in 77% of cases the category of the sensitive web pages visited can be identified based solely on the labels in the browsers' ad profile.
Kyle Crichton, John Krumm, and Siddharth Suri. Inferring Sensitive Browsing Information from Online Advertising Profiles. 2023. In Submission.
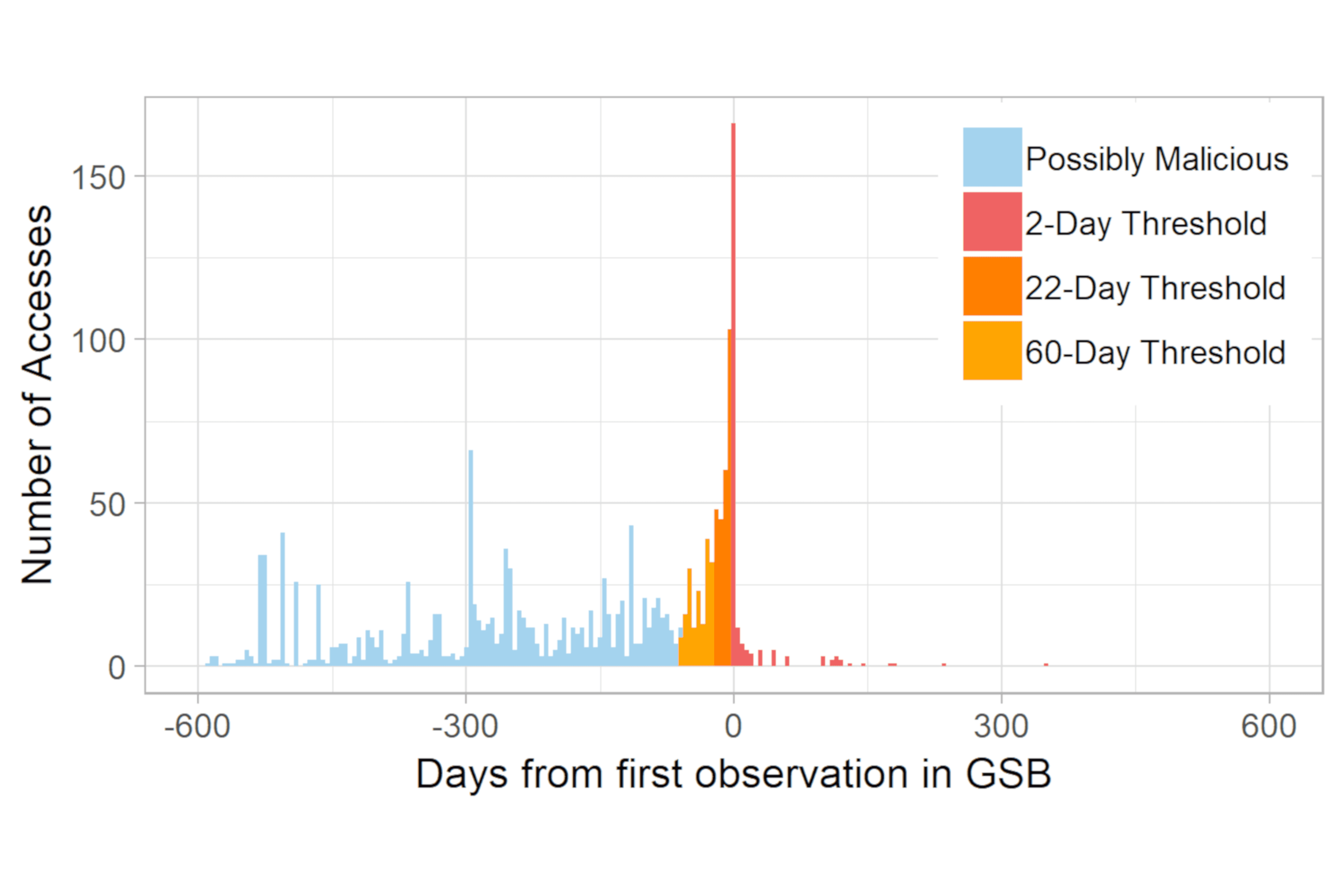
To keep users safe online, current protections frequently employ blocklists of known malware and phishing websites. However, such defenses suffer from an inherent gap between malicious content creation and its detection, leaving a window where users are left vulnerable. To address this limitation, our work introduces a method of detecting exposure based on a user's web browsing. Using sequential temporal modelling, our work not only improves classification performance by a significant margin (between 93% and 145% F1-score improvements, and 15-18% AUC improvements) over previous models, but also maintains strong robustness across completely disparate sets of users. Furthmore, our models show strong resilience to concept drift, as their performance holds steady over multiple years of testing.
Kyle Crichton, Jin-Dong Dong, Akira Yamada, Yukiko Sawaya, Lorrie Cranor, and Nicolas Christin. Accurate, Generalizable, and Practical Behavioral Models to Identify Impending User Exposure to Malicious Websites. 2023. In Submission.
In the design of qualitative interview studies, researchers are faced with the challenge of choosing between many different methods of interviewing participants. While previous work has anecdotally compared the advantages of different online interview methods, no empirical evaluation has been undertaken. To fill this gap, we conducted 154 interviews with sensitive questions across seven randomly assigned conditions, exploring differences arising from the mode (video, audio, email, instant chat, survey), anonymity level, and scheduling requirements. We find several qualitative differences across mode related to rapport, disclosure, and anonymity. However, we found little evidence to suggest that interview data was impacted by mode for outcomes related to interview experience or data equivalence. The most substantial differences were related logistics where we found substantially lower eligibility and completion rates, and higher time and monetary costs for audio and video modes.
Maggie Oates, Kyle Crichton, Lorrie Cranor, Storm Budwig, Erica J. L. Weston, Brigette M. Bernagozzi, and Julie Pagaduan. Audio, video, chat, email, or survey: How much does online interview mode matter?. PLOS ONE 2022. View Here
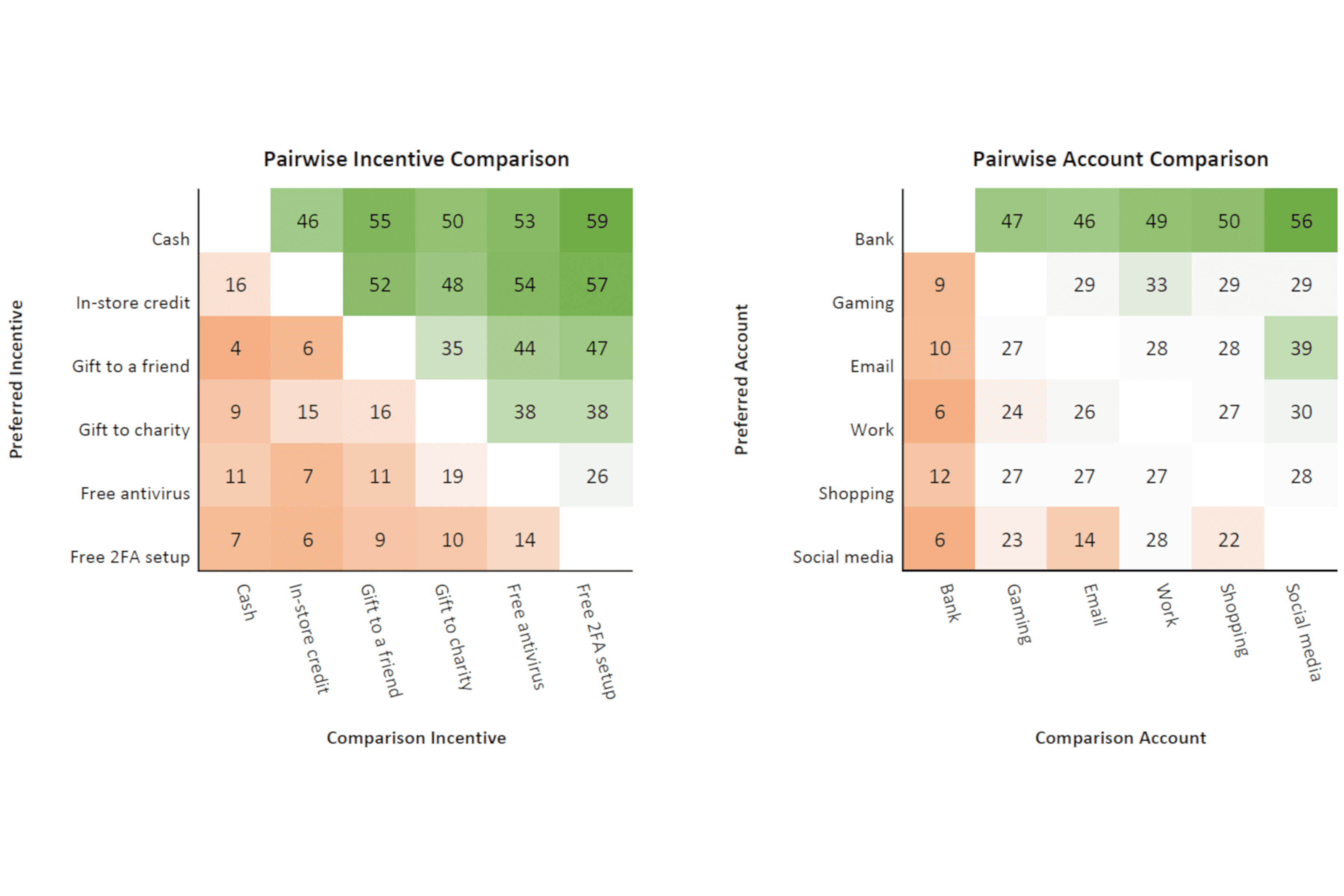
What originally started as a course project inspired by a mutual love of video games became a small research project assessing the effectiveness of incentives for people to adopt two-factor authentication (2FA) in online gaming. The study surveyed gamers who regularly played the massively popular multiplayer game Fortnite to assess their perceptions of a free in-game emote that was being offered by Fortnite's parent company to get players to enable 2FA on their account. While we found that the effect of the incentive was not statistically significant, likely a result of poor end-user communication, we observed strong social effects within the gamer community: if a player knew another player who had adopted 2FA they were much more likely to 1) know about the incentive and 2) have adopted 2FA themselves.
Kyle Crichton, Jason Lee, and Meihan Li. 2019. Incentives for Enabling Two-Factor Authentication in Online Gaming. Extended Abstract. SOUPS 2019. View Here